Demonstrate cyber security risks associated with trendy micro and local 5G introduction
Here's My Content
On October 26, the Trend Micro held an online briefing session for news organizations to explain cyber security risks with the introduction of a local 5G (5th -generation mobile communication system used in specific areas).

"Core networks in the Core Network," said Yohei Ishihara, the company's security e -graist, in a demonstration experiment conducted in June 2021 that "attacks with core networks can be destroyed and interfere with manufacturing."He said that he would recommend strengthening security.
トレンドマイクロ セキュリティエバンジェリストの石原陽平氏Mr. Ishihara defines the mobile communication network as "a communication system that can continue communication even if the user moves", and then "Core Network (CN: CN: Command Tower for the entire System)", "RAN: RAN: Ran: Ran: Wirelessly Wireless)Introducing the fact that it consists of three elements: "network composed of base stations)" User terminal (UE: SIM terminal, Telecommunications with RAN) ".
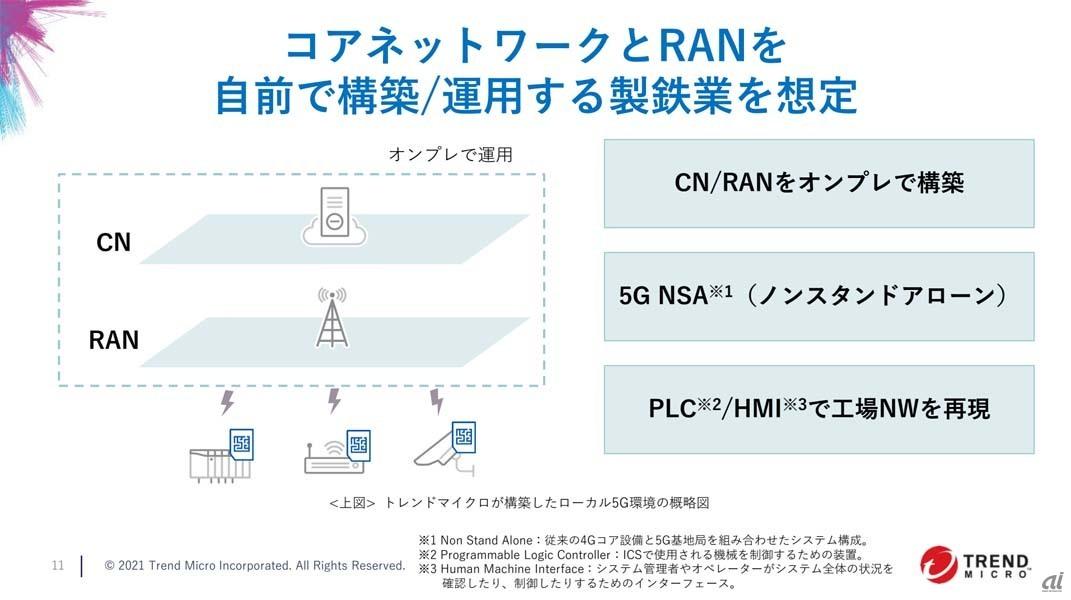
移動通信ネットワークの構成。無線基地局は街中で見かけることもあるためまだ馴染みがあるが、コアネットワークに関しては関心を持たない人も多いだろう。しかし、重要な情報が集中することから、攻撃対象となることを想定して防御する必要があるという(出典:トレンドマイクロ)In the conventional mobile phone network, the core network and wireless access networks are built and operated by telecommunications carriers as service infrastructure, and users did not clearly aware of their existence, but in the local 5G, these are these.He also pointed out that users need to build and operate themselves, and because they are unfamiliar environments, there is a high possibility that settings and operation mistakes will occur.
In the demonstration experiment, it was confirmed that the environment was to build an environment assuming "steel -constructed core networks and RAN on their own", and as a result of attacking according to the expected scenario, it could have a serious impact.。In the local 5G, various components that make up the core network are also expected to use general -purpose hardware and open source software, and vulnerabilities and setting mistakes may have an intrusion route to the core network.If you are invaded by the core network, there is a risk of being intercepted in a flat text inside the core network, and you will be tampered with.For example, it has been confirmed that it is possible to interfere with the operation of the device and the manufacturing process by falsification of the environmental data referenced by the manufacturing equipment and equipment, causing quality problems and obstructing manufacturing.
実証実験の舞台となった環境。実際にローカル5G環境を構築する際に使われるであろう一般的な機器に加え、製造業でよく使われている環境であるPLC/HMIで構成されたOTネットワークも再現したという(出典:トレンドマイクロ)Mr. Ishihara also said that the attacker aimed at the core network was "the foundation that deals with information that directly affects the confidentiality, availability, and perfection of the manufacturing process," and "once constructed, it was difficult to renovate and correct it.He pointed out two points, saying, "The impact is large," and pointed out that "it is necessary to prepare for targeted attacks."He also said that "security measures on the premise of invasion" were important.
It has been reported that ransomware damage is becoming more severe over cyber security, and the manufacturing industry has caused enormous damage to the factory suspension.Many of these damage can be said to have been caused by the fact that attacks targeting IT infrastructure could not be prevented.In the attack on local 5G, which was the theme this time, the risk of interfering with the system on the control technology (OT) side such as production equipment was pointed out.In addition to the measures on the IT side that will have been implemented so far, the OT environment will not be connected to the Internet as before, assuming the risks that will be targeted as cyber attacks in the future.It is a form that clarifies the current situation that the idea of maintaining security is no longer applicable.
検証結果のまとめ。コアネットワークに侵入を許してしまうとセンサーデータなどの改ざんを受けるリスクがあり、結果として自動制御されている生産設備や機器等の動作に干渉される可能性がある(出典:トレンドマイクロ) ゼロトラストの発想と同様に、侵入を前提としたセキュリティ対策を講じることが推奨される(出典:トレンドマイクロ)ZDNET JAPAN article is read by email every morning (free registration)
メールマガジン購読のお申し込み