
McAfee New Android Malware Targeting Users in Japan and South Korea New Android Spyware Used in MoqHao Phishing Attacks Targeting Japan and South Korea Discovered on Google Play Store Fake Japanese Security App Distributed on Google Play Fake South Korean police app Link to existing phishing campaign Conclusion Appendix
McAfee's mobile research team discovered a new type of Android malware used in a phishing attack called MoqHao (also known as XLoader and Roaming Mantis) targeting users in South Korea and Japan. While a series of phishing attacks, primarily targeting Japanese users, are still active, the new spyware discovered this time has very different characteristics from the MoqHao malware that has been used so far. . All of the spyware discovered this time targeted users in Japan and South Korea, disguised as security-related apps. As evidence suggesting a link between existing phishing distribution methods and this spyware discovery, McAfee published a phishing page associated with a DNS hijacking attack that enticed users to install spyware distributed on the Google Play Store. I found
McAfee discovered two fake security applications distributed on the Google Play store. Its package names are com.jshop.test and com.jptest.tools2019. With the help of the Google Android Security team, these spywares were removed from the Google Play store immediately after they were discovered, so the number of downloads of the applications was very low, minimizing the damage.
Fake security application distributed on Google Play
This spyware for Japan has the following four commands and control functions. Spyware collects device information such as IMEI and phone number, and also attempts to steal SMS/MMS messages sent and received on the device. These malicious commands are sent to infected devices from Tencent push notification service.
Command registration to mCommandReceiver class
In order to evade Google's security review and distribute spyware on the Google Play store, cybercriminals first implemented and released the minimum necessary functions.
As a result of our further investigation, we discovered a spyware sample targeting Korean users that is very similar to the spyware for Japan. We discovered that the South Korean spyware was distributed as an anti-spyware application for the South Korean Police Department, and that the spyware file was distributed as cyber.apk on a host server in Taiwan. Icons and package names com.kpo.scan and com.kpo.help used in the discovered spyware suggest that it is disguised as a South Korean police app and intended to deceive users.
Korea police app icon abused
Spyware for South Korea is obfuscated using Tencent's obfuscation tool to hide malicious code. As a difference from existing MoqHao samples, the existing sample obtained the address of the C&C server via the Twitter account, but the spyware discovered this time directly embedded the address of the C&C server. I was.
This spyware for South Korea, like the spyware for Japan, uses the Tencent push notification service to send commands to infected terminals. Compared to the one for Japan, many commands are implemented.
Tencent Push Service
The figure and table below explain the C&C commands implemented in the spyware and their actions.
Command registration to mCommandReceiver class
In addition, the spyware for South Korea has implemented some interesting functions. First, to achieve automatic call placement, the KAutoService class had an implementation to check the app in the frontmost active window and automatically click the Start Call button.
KAutoSevice class automatically clicks the call button in the foreground calling app
The second interesting function was implemented to disable anti-spam applications (for example, whowho–Caller ID & Block) to warn users about incoming calls from unknown phone numbers. By disabling anti-spam apps, users are no longer alerted to incoming calls from suspicious phone numbers, facilitating social engineering scams by cybercriminals. prize.
Code to disable anti-spam application (1)
Code to disable anti-spam application (2)
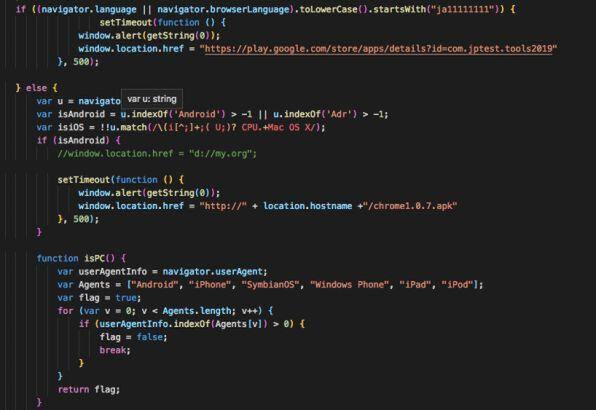
The characteristics and structure of these spyware are very different from existing MoqHao samples, but we were able to find a connection between this new Android spyware and the currently active MoqHao phishing and DNS hijacking attacks. Many thanks to @ZeroCERT and @ninoseki for the information on this. According to the provided information, a server-side script on the phishing site hosting the fake Chrome app could, under certain conditions, redirect users to a fake security application published on the Google Play store (https://play. google.com/store/apps/details?id=com.jptest.tools2019).
Code that directs to a fake security app on Google Play in a server script (source: @ninoseki)
In addition, there is a strong correlation between the spyware for Japan and South Korea discovered this time. A common spy command string was used, along with the same access keys for use with cloud services. As such, we can conclude that these spywares are related to the ongoing MoqHao phishing campaign.
The purpose of this spyware is to disguise itself as a security application and perform spying activities such as tracking the device's location and eavesdropping on conversations. Phishing attacks by cybercriminals are still being observed today, and the attempt to distribute newly created Android spyware through official stores trusted by users is a cybercriminal orchestrating MoqHao phishing attacks. can be regarded as one of the major signs in
In order to protect your privacy and protect your data from cyberattacks, do not install apps from other than official application stores. Keep your firmware up to date and install security software to protect your device from malicious apps.
McAfee Mobile Security detects this threat as an Android/SpyAgent, alerts mobile users, and prevents data loss. For more information on McAfee Mobile Security, please visit https://www.mcafeemobilesecurity.com.
Code that directs to a fake security app on Google Play in a server script (source: @ninoseki)
*The content of this page is the content of the following McAfee Blog updated on August 7, 2019 (US time). Original: MoqHao Related Android Spyware Targeting Japan and Korea Found on Google Play Authors: Chanung Pak and Yukihiro Okutomi
