
Identity verification without the user's knowledge Improves convenience with invisible multi-factor authentication --Nikkei Cross Tech Special
Not only Kikyohara technology development, but also human wave tactics will be used to improve efficiency and sophistication, and increase the success rate of attacks. Through the latest trends in cyber attacks explained in the second and third sessions, I realized once again what kind of threats society is exposed to. Enhancing safety is becoming an increasingly important management issue for businesses that provide online services.
Okamoto As you pointed out. It is a matter of life and death if an incident damages trust and causes users to leave.
However, it is undeniable that too much safety awareness may lead to similar results. As a result of strengthening security, the convenience of the service is greatly reduced. It is a situation where users leave due to inconvenience.
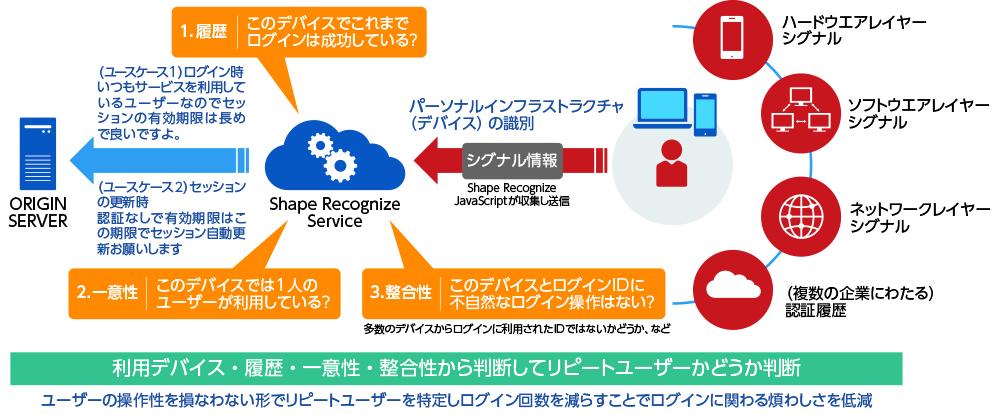
Kikyohara Certainly, it is said that there is a trade-off between enhanced security and user convenience.

Okamoto SMS (Short Message Service) is a typical example of sending a one-time password. The user must have a mobile phone at hand and enter the password within the time limit. You might think that's about it, but there are definitely users who will switch to a purchase on another EC site after failing to log in once. As a result of increased security for users and businesses, business opportunities are lost. For this reason, it is said that the multi-factor authentication mechanism using SMS is unpopular overseas.
Kikyohara It is ironic that trying to protect the business will hurt the business.
Okamoto It's not just business. Currently, elementary and junior high schools are beginning to introduce educational programs using PCs and tablets, but it seems that something similar is happening here as well.
For example, it is not easy for children in the lower grades of elementary school to remember multiple IDs and passwords for logging in to devices and learning content. Even if you can remember it, if it takes a long time to log in, it will put pressure on the limited class time. The safety mechanism hinders the effective use of the device.
Therefore, I hear that there are some cases in which children are instructed to operate contrary to digital literacy education, such as sticking a sticker with an ID and password on the device.
