
Basic knowledge of WAF
I still use a slightly older web application, but there is no longer a developer company.I heard that attacks aimed at web applications are being sophisticated, but I don't know how to deal with them.A vulnerability was found, but it cannot be corrected immediately.Meanwhile, many people are considering WAF to increase security as much as possible.In this series, we will explain the basic knowledge of WAF six times.The first one will explain what the effects will be when you actually use WAF.
Lottery
1st: What is WAF (Web Application Firewall)?
1.Web application vulnerability
Software is indispensable when using a computer, as the word "if you don't have a computer or software" is the word "just a box".Many people use not only Windows OS, but also office software such as Word and Excel, web browsers and PDF browsing software, as well as image processing software and New Year's card creation software.And web applications used via the Internet are also software.
With many convenient software developed, these are almost always bugs.Large -scale software, such as Windows, offers correction programs every month.In addition, smartphone apps often correct not only functions but also bugs.Everyone will notice if the user does a different operation from the functions expected, but this is not the only one.What we discuss here is a security defect and is called vulnerability.Many do not notice their existence.However, if the attacker notices it and abuses it, various damage such as virus infection, information leakage, and falsification will occur (Fig. 1).
図1:不具合と脆弱性の違い(引用:増井敏克、図解まるわかりセキュリティのしくみ、翔泳社、2018年、P.97)This vulnerability is not only an attacker, but ...
>>第1回 第1章の続きを読む(PDFダウンロード)
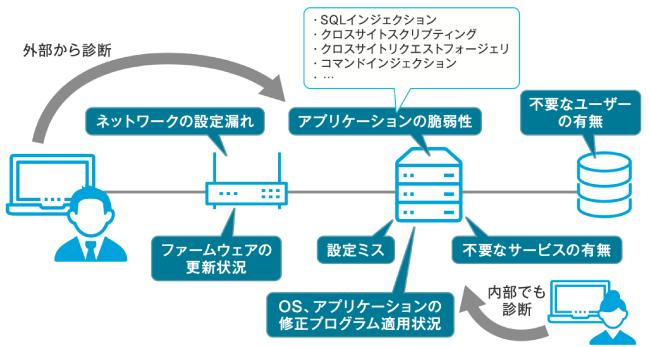
2.Things that can be protected by vulnerability diagnosis
When developing software, the developer will test.The general test is to confirm that the expected operation works correctly.In other words, it can be detected by testing if it is a defect in general use.However, vulnerabilities that are security defects cannot be detected.Therefore, in addition to the normal test, it is necessary to check that there is no vulnerability from the attacker's point of view.This is a vulnerability diagnosis (Fig. 3).This time, we will focus on vulnerability diagnosis for Web applications, but in fact, vulnerability diagnosis is also performed for desktop applications and smartphone apps.
図3:脆弱性診断(引用:増井敏克、図解まるわかりセキュリティのしくみ、翔泳社、2018年、P.113)Vulnerability diagnosis includes an automatic diagnosis that uses a tool to perform mechanically using a tool and a manual diagnosis in which an expert tests manually from an attacker's perspective.In automatic diagnosis, ...
>>第1回 第2章の続きを読む(PDFダウンロード)
3.WAF effect
Vulnerability that occurs during development may be prevented if the developer is careful.In fact, we do tests and reviews to reduce vulnerabilities as much as possible.However, since the developer is a human, all vulnerabilities cannot be removed.In addition, even if there is no problem during development, the appearance of a new attack method may cause vulnerable parts.
Many vulnerabilities can be found by performing vulnerability diagnosis such as automatic diagnosis and manual diagnosis.Still, there may be leaks.If there is a vulnerability, it is easy to point out, but it cannot be said that it does not exist because it cannot be found.It is difficult to prove that it is not, as it is called "proof of the devil."Even if a vulnerability is found, it may not be possible to fix it.Various reasons can be considered, such as the company that developed the web application, the lack of the cost of correction, and the time it takes time to fix it.
The introduction of WAF (Web Application Firewall) is considered.WAF is as the name suggests ...
>>第1回 第3章の続きを読む(PDFダウンロード)
2nd: Various types of WAF
Last time, we explained the vulnerability of web applications and the effects of WAF.How do you choose WAF when considering the introduction of WAF?There are three major types of WAF depending on how they are installed and installed.Each has its advantages and disadvantages, so it is necessary to choose the optimal type after considering the introduction cost, running cost, convenience, etc.This time, I will explain these three types.
1.Software type WAF
Since the web application is running on the web server, it is possible to first introduce WAF on this web server.In other words, software with a WAF function installed on the web server checks the communication content when executing a web application.This is a software type WAF (Fig. 1).It is sometimes called a host type because it is introduced in a computer.
図1:ソフトウェア型のWAF(引用:独立行政法人情報処理推進機構セキュリティセンター、Web Application Firewall(WAF)読本、2011年、P.17)The advantage of this method is ...
>>第2回 第1章の続きを読む(PDFダウンロード)
2.Network type WAF
If you do not want to increase the load on the Web server or avoid introducing a new software on the web server, you can install a dedicated device.It is called a network type in a method of introducing the web application that is running on the route between the web application and the Internet (Fig. 2).Alternatively, it is sometimes called an appliance type or a gateway type.
図2:ネットワーク型のWAF(引用:独立行政法人情報処理推進機構セキュリティセンター、Web Application Firewall(WAF)読本、2011年、P.16)Considering the role of firewall, installing it in the middle may be easier to understand as an image.actually,……
>>第2回 第2章の続きを読む(PDFダウンロード)
3.Cloud -type WAF that can be entrusted with operation
Cloud -type WAF has recently gained popularity as a way to solve the disadvantages of software type WAF and network -type WAF.Compared to the above -mentioned WAF, which requires operation and monitoring in -house, cloud -type WAF has the advantage of not only being able to manage external experts, but also only on monthly usage fees.The time it takes to introduce is short and you can start using it immediately.There is no need to introduce new hardware or software because you only need to change the network settings to go through a cloud -type WAF for access to our own web server.It is an image used as a service instead of the hardware introduced with a network type WAF.
However, while these benefits ...
>>第2回 第3章の続きを読む(PDFダウンロード)
3rd: Difference from other security technology
In the previous series, we found that WAF is effective to prevent attacks aimed at Web applications.On the other hand, if you have introduced other security technology, you may think that it is unnecessary to introduce WAF.However, each security technology has different types of attacks and the content to be protected.This time, I will explain what differences are there.
1.Difference from firewall
Because the name is similar, there is a firewall that is often confused with WAF (Fig. 1).Both are used to prevent external attacks, especially to prevent attacks on the network.For example, you can perform port scanning to check the vacant port of the server in order, and prevent unauthorized access to servers that cannot be accessed.
図1:ファイアウォール(引用:増井敏克、おうちで学べるセキュリティのきほん、翔泳社、2015年、P.72)Check with the firewall ...
>>第3回 第1章の続きを読む(PDFダウンロード)
2.Difference from IPS and IDS
Like firewalls, IPS and IDS are devices that prevent external attacks on the network.IPS is called an illegal invasion prevention system, and IDS is called an illegal invasion detection system, and has a function to defend and detect external intrusion.As the name suggests, the IDS only detects illegal access and notifies the administrator, whereas IPS prevents invasion, such as blocking the communication (Fig. 2).
図2:IPSでの通信の遮断(引用:増井敏克、おうちで学べるセキュリティのきほん、翔泳社、2015年、P.175)The illegal invasion here refers to an attack that sends a large amount of packets to the target server, such as DOS attacks and Syn Flood attacks, and hinders the normal movement of the server.At this time, even if you check the communication content one by one, there is no problem with the destination or source of the communication, so it cannot be prevented by firewall.And when the amount is large, ...
>>第3回 第2章の続きを読む(PDFダウンロード)
3.Difference from virus software
Considering that WAF prevents attacks aimed at web applications, it may be necessary to prevent other applications aimed at attacks.In fact, there are many attacks aimed at applications introduced on a personal computer.For example, not only Office software such as Word and Excel, but also attacks aimed at vulnerability such as Adobe Acrobat Reader and Adobe Flash Player.When aiming for the vulnerability of these applications, it is common to attack the files used there.Malware and virus can be considered as a means of attack.In many cases, an attack using a macro of Office software has been found to infect a virus by opening an email attached file, destroys internal files, or extracts personal information.
Looking at the movements and patterns that appear in the file when the file is opened, it is a virus software provided by a security company that determines that it is a virus.In the current PC, it is commonplace to introduce antivirus software.however,……
>>第3回 第3章の続きを読む(PDFダウンロード)
4th: WAF detection method
Last time, I explained the difference between WAF and other security technology.Since the attack pattern aimed at web applications is diverse, it is not easy to detect all of them with WAF.To respond to new attacks that appear one after another, you need to maintain the pattern to detect.This time, we will introduce the detection methods that WAF actually performed, various operations and monitoring methods, and their recent trends.
1.Blacklist method
When you want to check an unauthorized input, the first idea is to find out the common elements of the input.For example, if a problem occurs when an HTML tag is entered in the form, it is only necessary to enter the HTML tag.In this way, a method of preparing an attack pattern list that is judged to be fraud, and blocking or getting ridiculous when processing that matches the content is called a blacklist system.
The word "blacklist" is familiar to the scene where you create a credit card or make a loan.If you lose your credit due to overdue or bankruptcy in the past, a blacklist will occur.The person posted there will not be able to create a credit card or apply for a loan.
The same is true for blacklists on WAF ...
>>第4回 第1章の続きを読む(PDFダウンロード)
2.White list method
Contrary to the blacklist method, a method of permitted only communication that is judged to be normal is called a whitelist system.Since only those registered in the list are not allowed, it is not affected by the occurrence of new attack patterns.Furthermore, if you create an appropriate list first, you will not need to update the list unless the specifications of the web application change.However, as a pattern that can be input, it is necessary to register all normal patterns, such as the type, number of characters, and input format, so it takes time to create them.Actually, there is a product that has a white list creation function, so by repeating general communication several times, the WAF automatically generates a list based on the common content.Using these functions may reduce management costs.
Due to these simplicity, the white list method seems to be more popular than the blacklist method.Nevertheless, there are scenes that cannot be defined as a whitelist, so it is not better to use them according to the characteristics of the application (Table 1).
In addition, if the specifications of the web application or the additional function occur, ...
>>第4回 第2章の続きを読む(PDFダウンロード)
3.Pattern matching and use of AI
It is important to continue to create and update each list, both in the blacklist and the white list.This requires detailed knowledge of communication between web servers and web browsers and the content of the web applications.Instead of creating and updating these lists, WAF vendors are regularly performed.It is said to be a pattern matching by using a database of past attack patterns and extracting patterns that can be judged as an attack.Recently, services that use AI (artificial intelligence) have appeared to automate this judgment.By checking and analyzing normal communication and logs, the pattern of unauthorized access and the rules for defending are automatically updated.
Until now, a blacklist and white list were generated with human hands.This took a lot of time and often caused errors.AI can learn the characteristics of normal and attack from a large amount of logs, so you may be able to do the work you have done manually.It is possible to update the system 24 hours a day, 365 days a year without getting tired like humans, which can solve the problem of lack of human resources with specialized skills.
as mentioned above,……
>>第4回 第3章の続きを読む(PDFダウンロード)
5th: Examples of attacks that can be protected by WAF
Last time, I explained how to detect WAF.Many people may have the question of what specific attacks can be prevented when introducing WAF, and whether WAF is needed in the first place in the first place.Web applications will be attacked in various ways.This time, I will explain how to attack, especially for Web applications, and how WAF will prevent it.
1.SQL injection
Many web applications such as shopping sites, SNS, bulletin boards, and search engines use a database to save data.These web applications operate the database management system using the language SQL.If there is a problem with this SQL description in the program, the attacker sends a special description content and embeds the attack code in the SQL to give instructions that are not assumed by the developer.increase.This enables destruction of the database and extracting personal information.
In this way, an injection (injection) in which illegal instructions are injected into SQL is an attack method called SQL injection.For example, there is a web application with a login screen.It is a mechanism that can log in if the entered ID and password match, and it works without any problems if it is a general usage.However, by entering a value shown in Fig. 1 in the password column, you can log in without knowing the password if you know the ID.
図1:SQLインジェクションの例(引用:増井敏克、おうちで学べるセキュリティのきほん、翔泳社、2015年、P.260)At this time, in the web application, the following SQL was running.
When the above password was entered here, the password authentication was ignored and logged in.This is the SQL injection.If a symbol like "'" is entered, ...
>>第5回 第1章の続きを読む(PDFダウンロード)
2.Cross site scripting
In the user post -type web application, such as a bulletin board, other people can view the contents entered by the user.While it is a very convenient mechanism, if the user inputs the contents containing the HTML syntax and outputs it as it is, a problem will occur.HTML, which can freely post your favorite fonts and images for ordinary users, is useful.However, the attacker can post a program called a script.
When an attacker posts a script, a malicious process is performed when the user browses the post.For example, it is possible to steal the information of the user who accessed the website.As an example that is often used, ...
>>第5回 第2章の続きを読む(PDFダウンロード)
3.Cross Site Request Fouri
A word similar to cross -site scripting is the Cross Site Red Quest Fouri.This is also a vulnerability generated across multiple websites, but when posting the input content, it is not an appropriate check (Fig. 3).
図3:クロスサイトリクエストフォージェリ(引用:増井敏克、おうちで学べるセキュリティのきほん、翔泳社、2015年、P.266)for example,……
>>第5回 第3章の続きを読む(PDFダウンロード)
6th: WAF precautions
Last time, I explained an example of an attack that can be protected with WAF.This is the last episode, and we will explain what kind of operation and surveillance work will occur after actually introducing the WAF.WAF is not the end if it is introduced.Since the attack method changes one after another, web application specifications and functions will also occur.Tuning according to these is required, and the load on the server and the logs that are output must be monitored.
1.Occurrence of misconceptions
WAF misposen is fake positive and false negative.First, I will explain these two.When the WAF is introduced, the communication is blocked when the attack is detected.There is no problem if this is a blockage of an actual attack.However, it may be blocked even though it is not an attack.In other words, even though the general user is using it in normal way, it may cause misin detection and block it.This is called Foles Positive.In such a case, there is no problem if the user makes inquiries, but that is not always the case.An important customer may be separated from this misjudgment and simply leave because the system cannot be used.
Conversely, even though the attacker attacked, WAF may judge that it is no problem and pass it.this is,……
>>第6回 第1章の続きを読む(PDFダウンロード)
2.Operation cost required for tuning
What is often forgotten when introducing WAF is the cost of operation.Generally, the cost of the introduction, such as the price of WAF products and the labor costs for operation verification, is aware of the cost at the time of introduction.Although it is sometimes focused on the functional aspects, such as software type, network type, and cloud type that are WAF techniques, it is not the end of the introduction of WAF.
Regardless of whether the WAF operation form is a blacklist or white list system, maintenance of the list is essential.Not only when a new attack method appears, it is necessary to make a new review every time a web application specifications or additional functions occur.At this time, it is necessary to consider the maintenance costs and operating costs of WAF.In particular, labor costs for operations such as log confirmation and list updates will increase as the period becomes longer.
In general,……
>>第6回 第2章の続きを読む(PDFダウンロード)
3.Impact on the server
When the software type WAF is introduced to the server, the load on the server increases accordingly.If there is no problem if there is enough time in the specifications, if the access rapidly increases, the server may go down or it may take a long time to connect, so check the load.You need to do it.Check indicators include not only the response time from the website user, but also the throughput of the network and the server resource consumption.In particular, checking CPU usage, memory usage, and disk capacity in the server are often performed.
In many cases,……
>>第6回 第3章の続きを読む(PDFダウンロード)
