Discover a suspicious process in Process Monitor!
In the 34th and 35th, we introduced how to use the "Windows Sysinternals" tool to find a suspicious program based on automatic execution settings and communication situations.This time, I will introduce how to watch the process itself.
Search for viruses and spyware from process file registriesxes status
This time, we will introduce a method of exploring viruses and spyware from the behavior of the process, but this method is a bit difficult and very troublesome.Therefore, we recommend that you narrow down the target to some extent in the 34th and 35th methods, and then execute the suspicious program.
To see the behavior of the process and the status of access to files and registries, use "Process Monitor" in Windows Sysinternals.When you start Process Monitor, you start to record the behavior of the running process.
In the default setting, it will be output to hundreds of lines in a few seconds.
In PCs, many programs, including system processes, are constantly working, and as you continue to record, it will be a huge amount.So, first press Ctrl+E, stop the record, and clear the record with Ctrl+X.Next, set the Filter to record only the necessary processes.
Filter settings can be called by Ctrl+L.If you open the Filter settings, there are some contents that have already been set.This is a setting to avoid extra information such as Process Monitor's own record.Leave the settings and add the process you want to watch for the behavior.
This time, I tried "IE-Sethomepage.I would like to watch the behavior of the process "EXE".This tool is a pseudo spyware tool that changes the Internet Explore homepage."Process Name" "IS" "" IE-Sethomepage for Filter conditions.Set up to EXE "THEN" Include "and press" Add ". Then IE-Sethomepage.Since only the operation related to EXE is recorded, press Ctrl+E again to resume the record.
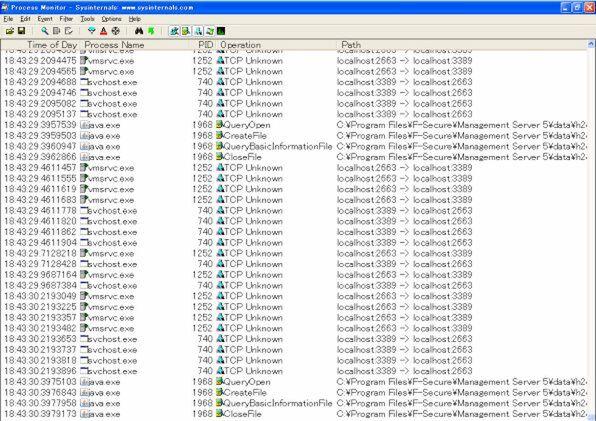
IE-Sethomepage in this state.If you execute EXE, you can see in detail what kind of action you are doing.
Settings to record only the movement of a specific process
The information is displayed in chronological order from the top, and you can see what kind of operation is performed in the Operation column, and which files and registrys are targeted in Path columns.
IE-Sethomepage.Following the behavior of EXE, you can see that the operation called RegSetValue, that is, the registry key setting is performed to "HKCU \ Software \ Microsoft \ Internet Explorer \ Main \ Start Page".If you display the details in Ctrl+P, you can see the newly set homepage address at the data.
Record of Internet Explore homepage rewriting operation
In this way, you can find out if the process that looks suspicious is really bad, for example, if you have accessed files such as personal documents or address books.
Not only viruses and spyware, but also for discovering P2P software
The method introduced in these three times is not only looking for viruses that could not be detected with antivirus software, but also helps find a virus other than a virus, for example, but dangerous software.Of course, you need to know the name of the P2P software.
At home, you can find out if the P2P software has been secretly moved in the background on the PC that the whole family shared and used.Companies can also be used to find out the use of software that is not related to work.
SysINTERNALS has not only useful for security, but also a variety of other useful tools.If you are interested, you should try other tools.
Author introduction: Yosuke Futasu
Fusecure Co., Ltd. Technology & Service Department Product Expert In 2008, joined Fusecure.He is mainly in charge of technical support for Linux products to his partner.
